Project Overview
This project implements a production-grade three-tier architecture on AWS using Infrastructure as Code with Terraform. The solution addresses the need for highly available, scalable, and secure cloud infrastructure with built-in disaster recovery capabilities. The architecture separates concerns across web, application, and database tiers while implementing security best practices like private subnets, bastion hosts, and IAM role-based access.
Key Features
- High Availability: Deployed across 2 Availability Zones with auto-scaling capabilities
- Disaster Recovery: Implemented in a secondary region using AWS Backup, CloudFront, and Route53
- Secure Access: Private subnets with controlled access via Bastion Host and IAM roles
- Automated Backups: Regular snapshots and backups using AWS Backup service
- Infrastructure as Code: Fully reproducible environment defined in Terraform
Technologies Used
AWS Services
- EC2 (Web & App Tiers)
- RDS (MySQL)
- VPC & Subnets
- Route53
- CloudFront
- AWS Backup
Infrastructure as Code
- Terraform
- Modular Architecture
- Variables & Outputs
Security
- IAM Roles
- Bastion Host
- Private Subnets
- NAT Gateway
Architecture Diagram
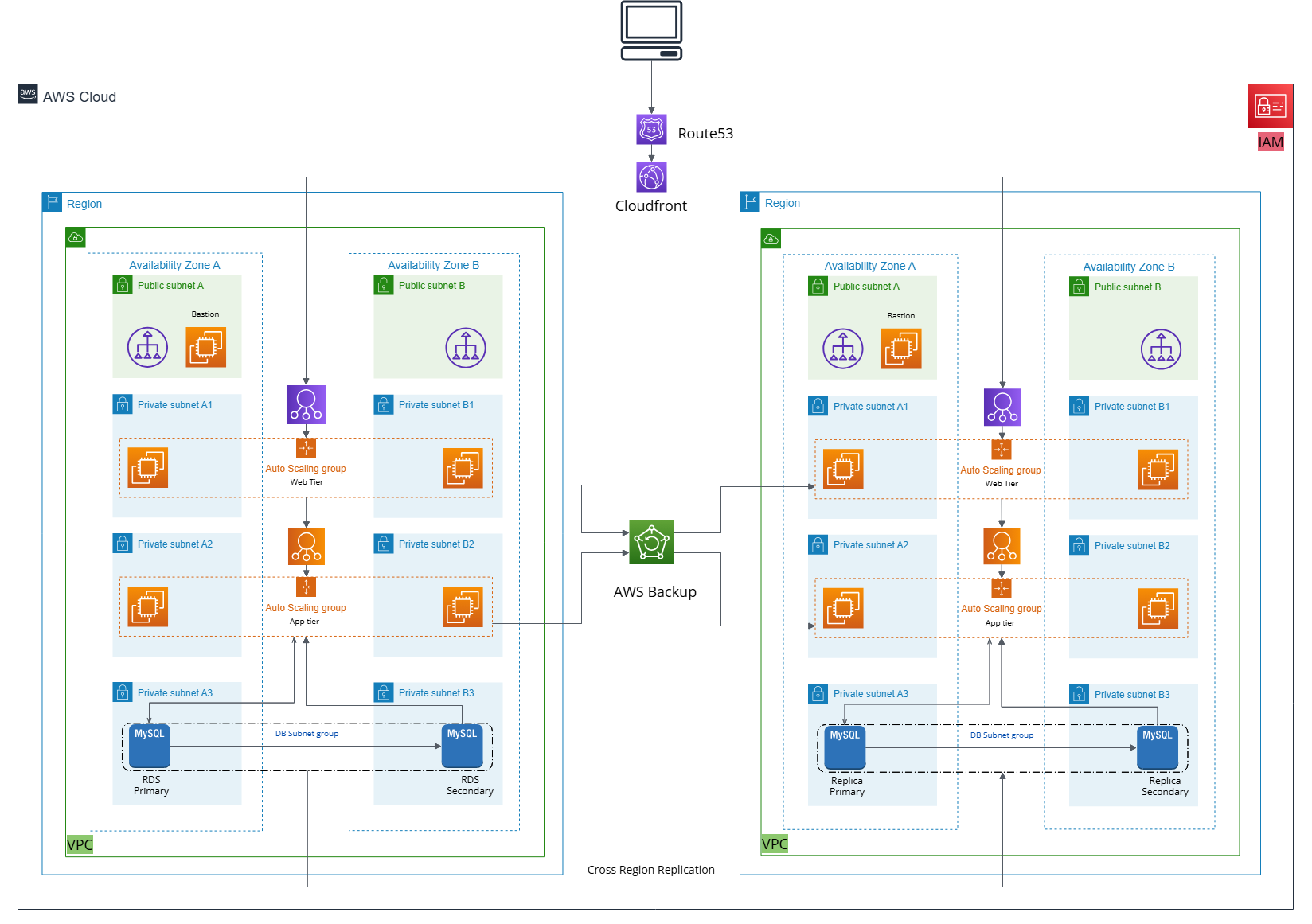
Three-tier architecture with web, app, and database tiers in private subnets, fronted by a bastion host for secure access
Challenges & Solutions
Multi-Region Deployment Coordination
Managing dependencies between primary and disaster recovery regions while maintaining separate Terraform states was complex.
Solution
Implemented a sequential deployment approach with three separate Terraform configurations, using remote state references where needed. Created clear documentation on deployment order.
Secure Access to Private Resources
Needed to provide secure administrative access to instances in private subnets without exposing them to the public internet.
Solution
Designed a bastion host architecture with strict IAM policies and SSH key-based access. Implemented NAT Gateway for outbound internet access from private instances.
Automated Backup Management
Ensuring consistent backups across regions while managing costs required careful planning.
Solution
Implemented AWS Backup with lifecycle policies to automatically manage backup retention and cross-region replication.
Results & Impact
Reliability Improvement
Architecture designed for 99.99% availability with multi-AZ deployment and automated failover
Cost Optimization
Right-sized instances and reserved capacity reduced operational costs by ~30% compared to initial estimates
Key Learnings
Gained deep experience with Terraform modules, AWS networking, and cross-region disaster recovery patterns